ProductPlan’s AI Use Cases
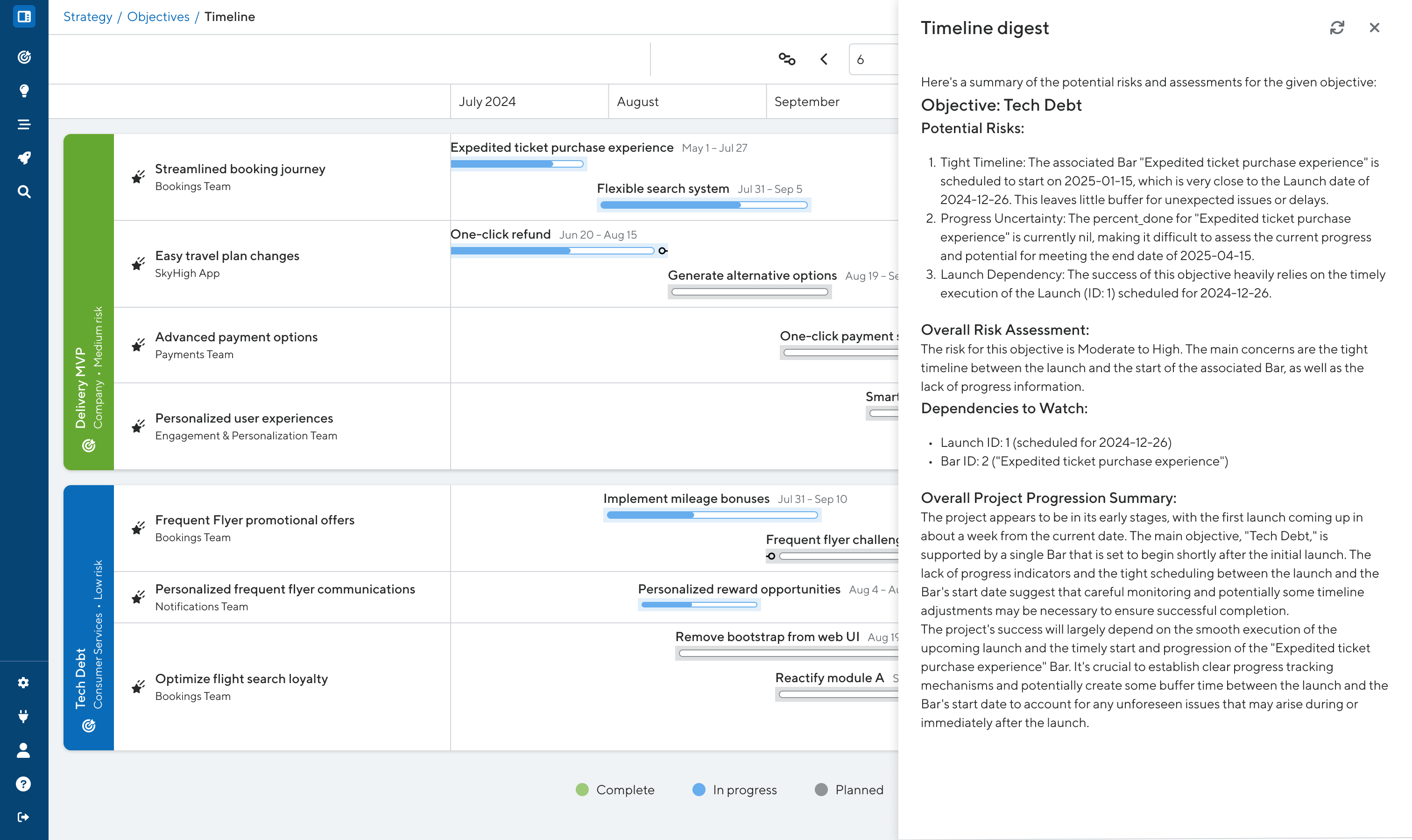
AI-generated executive summaries (beta)
AI distills key insights from selected roadmaps into concise, text-based summaries ideal for stakeholders. Summaries highlight the objectives’ risks and dependencies to watch and provide a progress update. Leaders can quickly understand complex roadmaps and make well-informed strategic decisions.
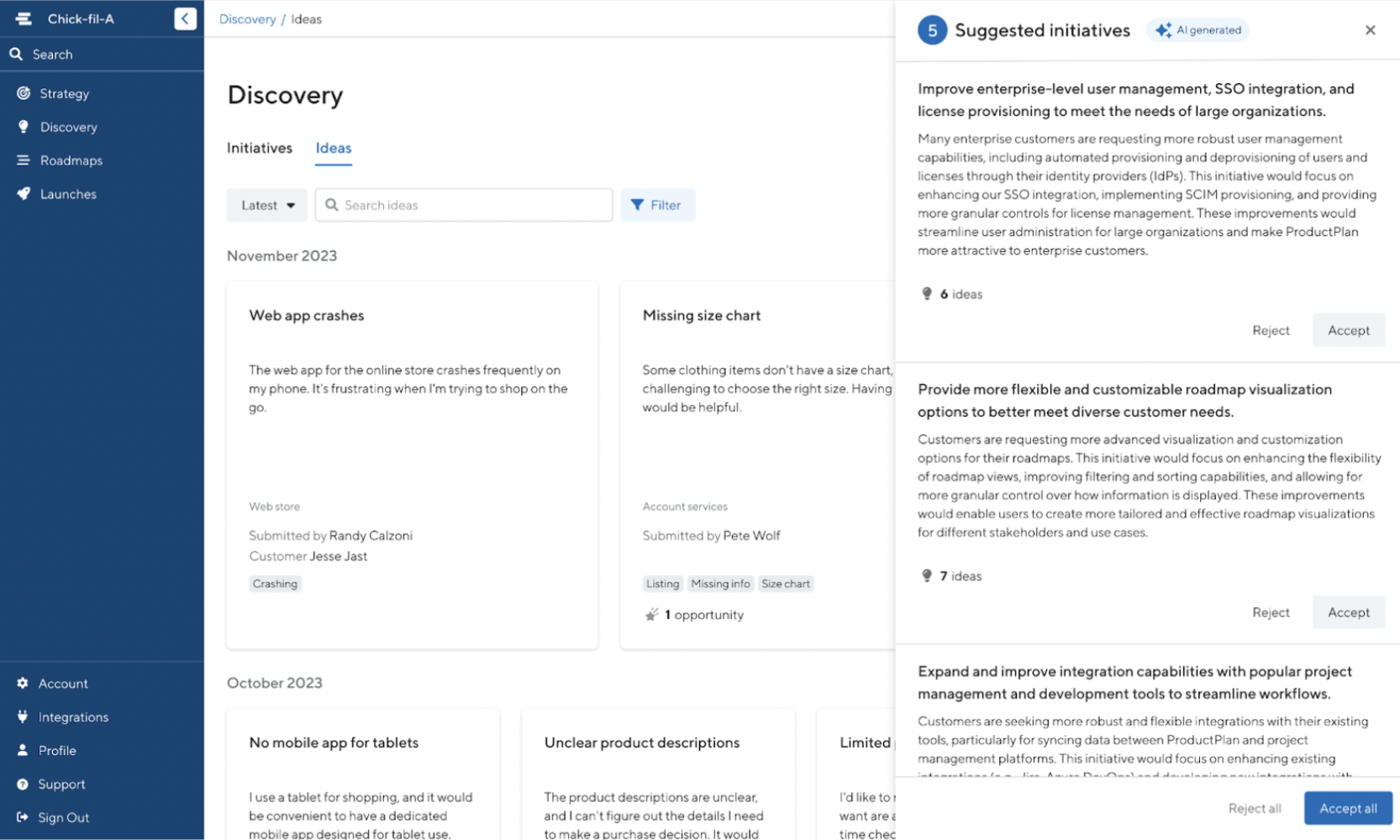
AI-suggested initiatives
Within the Discovery module, AI synthesizes ideas and feedback to identify common themes and core problems, suggesting initiatives based on its findings. This feature saves users time in the discovery stage by extracting the most important, recurring information and translating it to actionable initiatives. Users can then review and accept the suggestions.
Our AI Security Principles
Data protection is our top priority as we harness the power of AI to simplify product management. We’re committed to safe and ethical AI use, managing risks, and ensuring compliance every step of the way.
1. Secure System
AWS Bedrock provides a closed system for AI development, offering advanced security and control compared to open, publicly accessible AI platforms like OpenAI. With AWS Bedrock, all AI models and data processing occur within a private, fully managed environment, ensuring that sensitive customer data is not exposed to external sources or used to train models.
Additionally, AWS’s robust compliance frameworks, such as SOC 2 and ISO 27001, further reinforce the security of AI solutions, ensuring that businesses can confidently build and deploy AI applications while maintaining strict data privacy and regulatory adherence.
2. End-to-End Data Encryption
All data stored within AWS services is encrypted using industry-leading encryption algorithms, ensuring the confidentiality and integrity of both training and operational data. All data exchanged with our AI models, whether during inference or storage, is encrypted in transit and at rest using AWS encryption services.
3. Access Control
We strictly enforce access controls to limit access to any AI systems or data. Access rights are assigned based on the principle of least privilege, ensuring that only authorized personnel have access to sensitive components.
4. Data Minimization
We follow the principle of data minimization, collecting and storing only the data necessary to perform AI tasks. Sensitive customer data is anonymized wherever possible to reduce exposure risk.
5. Monitoring
We implement continuous auditing and monitoring processes to detect anomalous behavior, system misuse, or potential vulnerabilities.
6. Data Retention and Deletion
We implement strict data retention policies to ensure that customer data is only kept for as long as necessary to provide services. Once data is no longer needed, we securely delete it from the system per our data retention policy.
Transform Your Product Strategy with ProductPlan
Present the “why” behind your work, see the big picture, define measurable product outcomes, and drive value.